All Posts In Aws
In this article, we would like to share some issues we had and resolved during setting up AWS Lambda to use Amazon RDS Proxy.
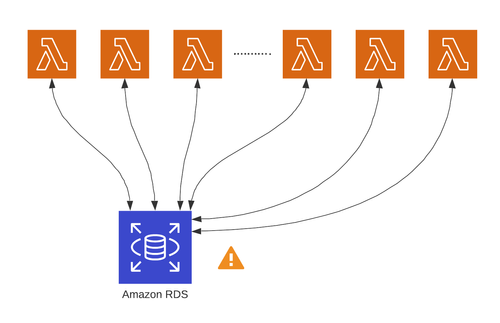
Starting for AWS Cloudwatch logs, we spent a week looking into 'Aborted Connection" errors on RDS. Finally, we figured out that although Lambda functions do not share a connection pool, the queries in the same function do share a connection pool, so we should keep on using the pool, but we should set the pool with min 0, so it could be destroyed without taking space. And the ultimate solution is to use Amazon RDS.
We have a serverless application running on AWS Lambda. Recently, we saw some warnings/errors in the AWS CodeBuild log as below, although the application is successfully built: provider.apiGateway.shouldStartNameWithService and gypErr. In the article, we will explain the issues and solutions.
In this article, we learned how to fix the 'failed to fetch' error from API-Gateway in our AWS Lambda Serverless Framework. The root cause is ended up to be the expired AWS Cognito Access/ID tokens. We were able to fix this by utilizing the Apollo Error Link to replace the old token with the refreshed one, and then retry the request.
AWS provides us Amazon Cognito User Pools, which could be used as authorizer to control access to our application. The article will explain all three tokens implemented by Cognito User Pools, and discuss some common questions of how to use those tokens.
My client's website is using AWS Amplify to handle the user log-in via AWS Cognito. As of aws-amplify-react@4.x.x, the Authenticator is not styled, so we had installed the aws-amplify/ui 2.0.3, and then imported the style from '@aws-amplify/ui/dist/style.css'. But it stopped working after updating to V3. Here is the solution.
Today, I learned that we could use @aws-sdk/client-ssm to retrieve Secrets from the secret manager as well. That is called Referencing AWS Secrets Manager secrets from Parameter Store parameters.
In the world of modern web development, keeping your tools and dependencies up to date is essential. Recently, I embarked on an upgrade journey, transitioning to npm v9 on my local machine. Little did I know that this seemingly innocuous upgrade would lead me to discover an issue with the AWS CodeArtifact command. In this blog post, I'll share my experience and the solution I found to make things right.