Serialize-Javascript Vulnerability FixAdam C. |
In the article: Upgrade Dependencies of Your NodeJS Application, we learned that Github Dependabot could detect and update packages that have known vulnerabilities. Not only it checks the package.json, but also the package-lock.json. Usually, when Dependabot finds the available update of the package to fix security vulnerability, it will submit an automated pull request.

One issue I found is that it's not very smart in the case of the vulnerabilities lying the package-lock.json, then it will not be able to automatically update them for us.
For example, I received one notification from Github Dependabot yesterday about:
Known high severity security vulnerability detected in
serialize-javascript < 3.1.0defined inpackage-lock.json.
But this time, there is no pull request because “Dependabot cannot update to the required version”
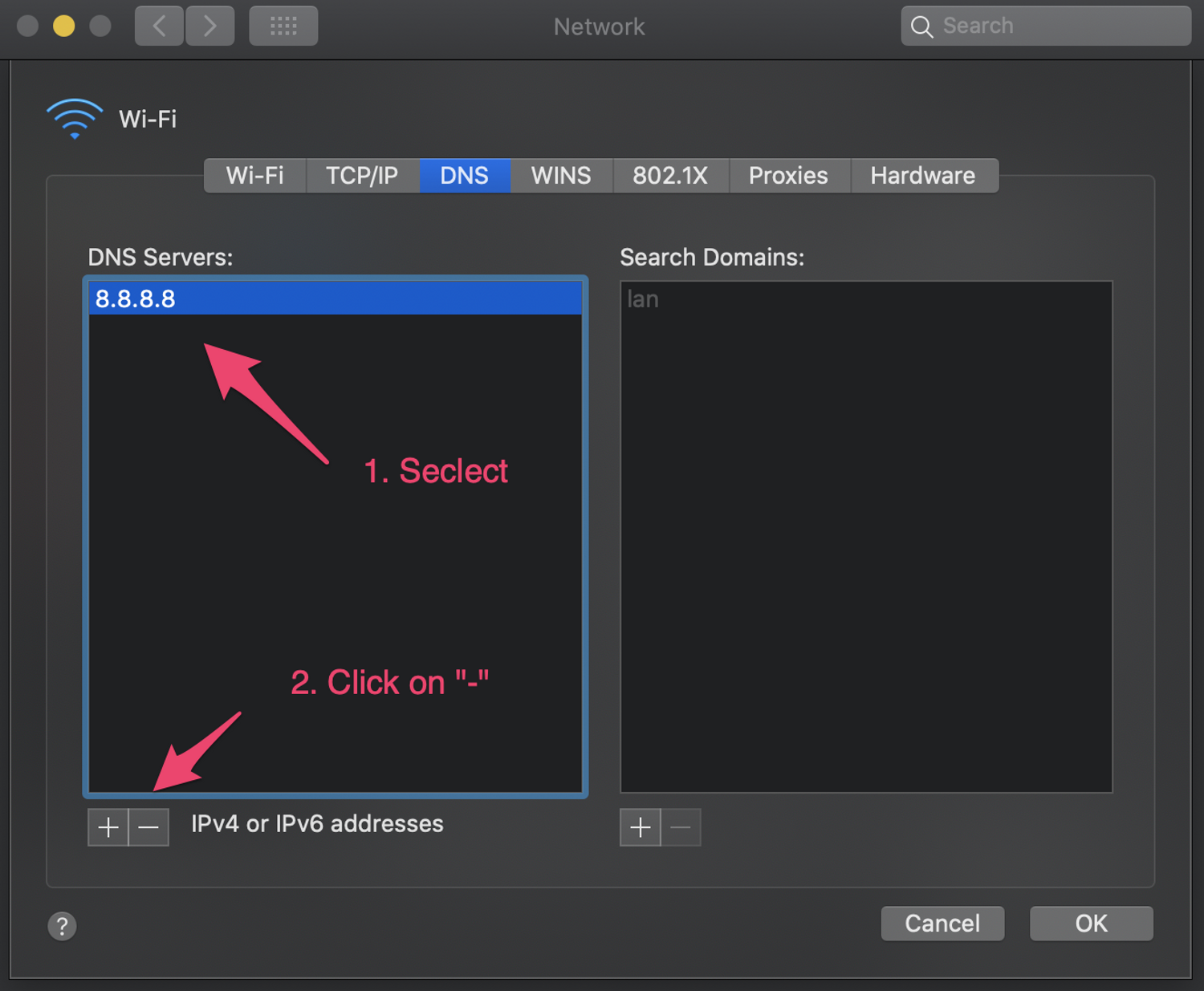
To fix this, I have to find out which main package (i.e., the package in the package.json) uses “serialize-javascript”. Here is a handy command we can use:
$ npm list serialize-javascript
feathers-dna@1.0.0 /Users/Adam/Projects/next-feathers/feathers
└─┬ mocha@8.0.1
└── serialize-javascript@3.0.0 Then I ran ncu, fortunately, there was an update for mocha, which is 8.1.1. After bumping mocha from 8.0.1 to 8.1.1, and I ran the same command:
$ npm list serialize-javascript
feathers-dna@1.0.0 /Users/Adam/Projects/next-feathers/feathers
└─┬ mocha@8.1.1
└── serialize-javascript@4.0.0 Toda! The serialize-javascript is updated to 4.0.0, which is higher than recommended 3.1.0. All done!
Update (9/20/2020)
The solution above did not work if “mocha” was not updated. In the other words, if the vulnerable dependency is a dependency of one of your dependencies, and the parent package does not update its dependency right away, then the above solution will not work.
This happens all the time, and one of possible solutions is manually updating the package-lock.json. If you uses yarn, then you may use “resolutions”. For npm, someone created npm-force-resolutions to support this, but as I tested, it does not work very well because it does not updated all vulnerable dependency to the latest in the package-lock.json.
Likely the best way to resolution this is to raise an issue (potentially with a PR to help them) with the maintainer of the parent package, then when they provide an update, update the dependency itself in your project. Unfortunately, this may take some time.
For example, currently, nextfeathers is pending node-fetch vulnerability fix.
next-dna@1.0.0 /Users/adam/Projects/next-feathers/next
└─┬ next@9.5.3
└─┬ @ampproject/toolbox-optimizer@2.6.0
├─┬ cross-fetch@3.0.5
│ └── node-fetch@2.6.0 deduped
└── node-fetch@2.6.0 And I see cross-fetch already had it fixed in 3.0.6, but toolbox-optimizer is not updated yet. next has it fixed in branch 'canary', but not in master yet.